Blog
Do you have something to share? Contribute to Falco blog!
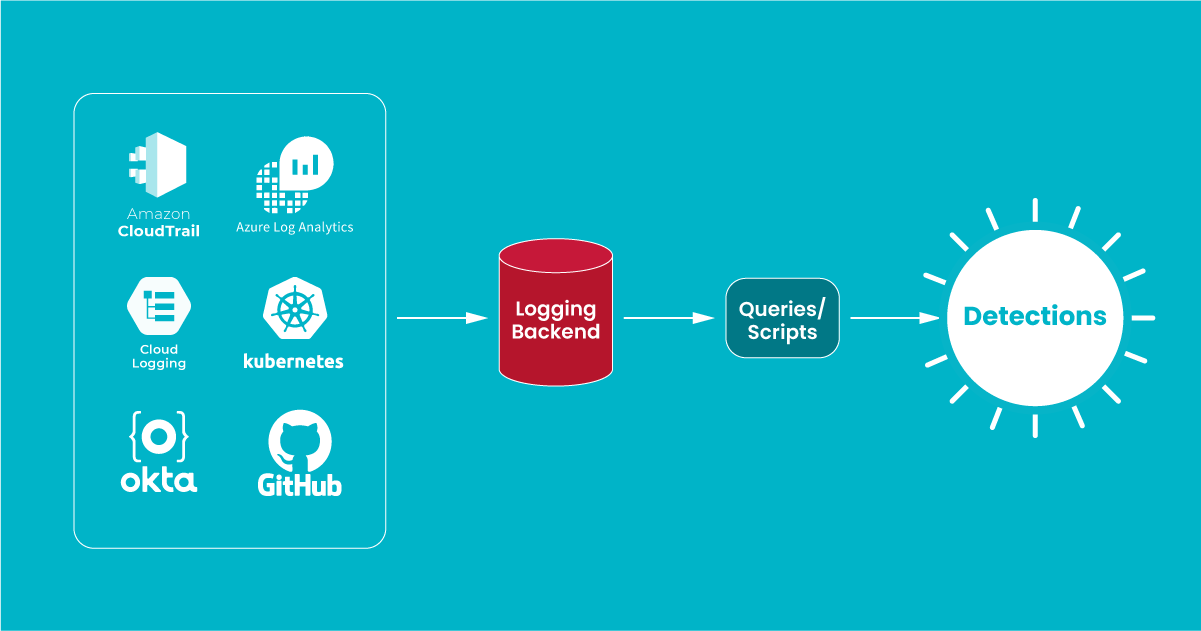
Understanding Okta plugin for Falco
Identity Threat Detection & Response (ITDR) in the cloud is of paramount importance to limit access to sensitive data and maintain the integrity of cloud infrastructure. Leading cloud providers like AWS, Microsoft Azure, and Google …
Adding runtime threat detection to Google Kubernetes Engine with Falco
One of the big advantages of running your workloads on a managed Kubernetes service like Google Kubernetes Engine (GKE) is that Google ensures your clusters are being deployed and managed following industry best practices. While GKE …
Falco Weekly 46 - 2023
This is the first of a series of weekly blog post whose aim is to give a quick overview about the development of Falco and its related projects. What happened in Falco this week? Let's go through the major changes that happened in various …
Introducing the new Falco training course, by CNCF, Linux Foundation, and Sysdig
Detecting Cloud Runtime Threats with Falco (LFS254) is the new Falco training course created by CNCF, Linux Foundation, and Sysdig. We're very excited about this new immersive course designed to enhance your expertise in securing …
Integrate Runtime Security into Your Environment with Falcosidekick
If you’re looking to integrate runtime security into your existing environment, Falco is an obvious choice. Falco is a Cloud Native Computing Foundation backed open source project that provides real-time threat detection for cloud, …
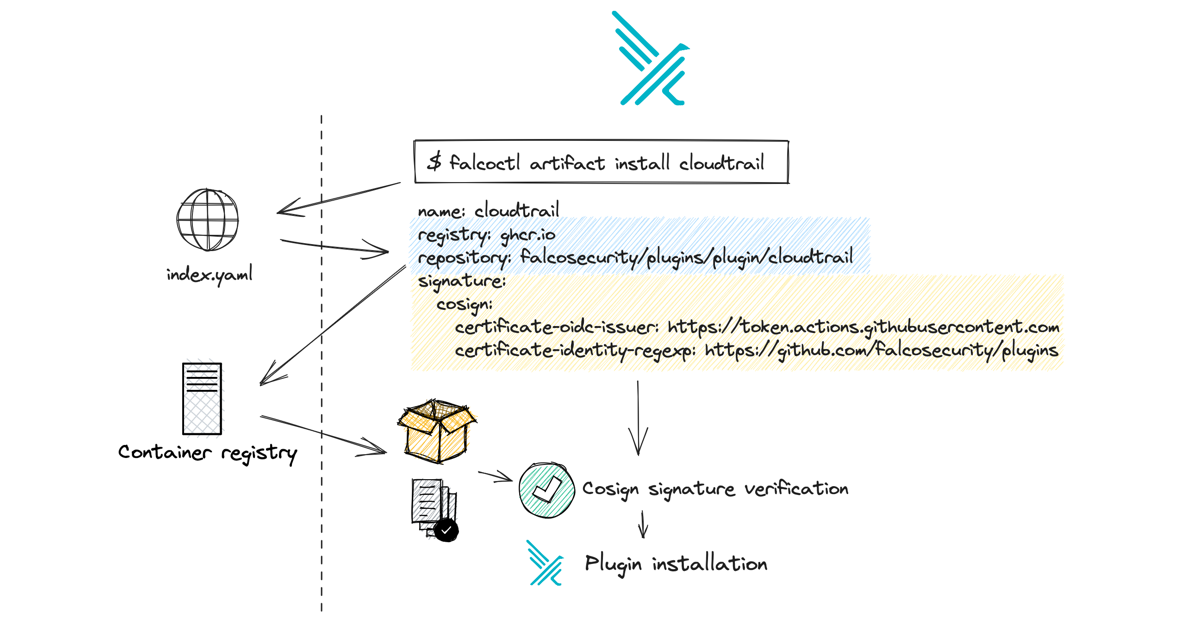
How we Sign and Verify Falco Plugins and Rules
Falco v0.36.0 and the Software Supply Chain (SSC) security The latest stable Falco release, v0.36.0, alongside falcoctl 0.6.1 and the 0.7.0 Helm chart introduced new features and improvements to the security of Falco's software supply chain …
Linux Introspection - From BPF to Wireshark to Falco
Falco, an open source innovation, was conceived with the vision of crafting a flexible and robust rules engine atop the Sysdig libraries. This initiative aimed to furnish a potent tool for the detection of aberrant behaviors and intrusions …